
The Future of Advanced Intelligent Networks:
The role of AI in the Provisioning of Value-Added Services in Third Generation Mobile Networks
M.D. Murwira (BSc. Eng. (Hons),MSc. COM. Eng,MIEE,AMIEE,ZIE)
Econet Wireless Value-Added Services Department
Senior Engineer Value-Added Services
- Analysis of Intelligent Networks and Cellular Systems
- Artificial Intelligence in Automatic Test Systems (ATS)
ABSTRACT
An illustration of the structure of IN networks and the definition of an IN service as looking beyond the traditional "enhanced services", such as call waiting. Service providers must move into new markets since traditional telephone services are no longer growing much, and to survive in the market place ,many providers are looking for new services that will meet the customers’ needs and bring in revenue. The complete merging of the Computing and Telecommunications fields has become irreversible with computing concepts like Database, networking and AI technologies being completely integrated with telecommunications concepts like SS7 and ATM. The role of AI is shown as a catalytic and glue technology beyond the 2000 millenium milestone among other technological advancements in the related IN sub-fields. Developments in fields like electronic commerce and the Internet coupled with advances in fast-processors and high bandwidth media makes IN the network of the future.
Outstanding characteristics of the IN are illustrated showing an extensive use of information processing technigues and network resources, integration of service creation and implementation by means of reusable standard network functions. The use of standardised communications between network functions, via service-independent interfaces and service subscriber control of subscriber-specific service attributes, in terms of definition and deployment is highlighted
1 INTRODUCTION
The IN Conceptual Model is a foundation of historical IN developments. The Service Plane represents an exclusively service-oriented view of the IN, which does not contain any information regarding the implementation of the network’s services. The Global Functional Plane provides a view of the different functionalities of an IN network. In this plane, the network is considered as a single entity, and this plane contains the call-processing model and service independent building blocks (SIBs). Service logic denotes all the service specific logic functions. Distributed Fuctional Plane provides a view of the distributed functions of the IN. This view is used to define the functional entities (FEs),their actions (FEAs), where an FE represents a grouping of related FEAs, and their relationships or information flows. The Physical Plane models the physical aspects of the IN structured network. It identifies the different types of physical entities, the functional entities they realise, and the protocols by which they communicate.
A brief survey is made on the existing IN or Value-Added Services ,servicebuilders and service integration. The role of the SS7 networks in relation to the protocol layers and OSI model and the effects of the ATM revolution are discussed. Dependence of the Future IN on other technologies is illustrated in areas of wideband code division multiple access (WCDMA) radio technology, fast VLSI chip technologies, high bandwidth circuits and transmission media, knowledge and database technologies, computer networks, object-oriented finite state machines, CORBA, TMN, UMTS, ODP and TINA. References are made to particular evolving models including those at Bellcore ,ITU-T and in Japan. The role of X.700 and CMIP in IN as network management tools and enhancements of IN operations.
The objectives and goals of IN are discussed ,showing the need for increased service velocity to enable market-driven, rapid introduction of new services, from conception to development. Broadening the range of services to go beyond the traditional voice and data bearer services to a much broader range, including information services, broadband and multimedia bearer capabilities.
Enabling a multivendor, competitive enviroment to ensure that the services will work correctly and consistently on any vendor’s equipment, across several vendors’ equipment. Evolution-type of development from existing networks such that the deployable technology would interwork with and evolve from existing networks since these cannot be replaced overnight.
The use and importance of AI in IN resource management, service building & management. IN TMN is shown as expert driven (knowledge-based or rule-based) and pattern analysis-based in reference to its five management functional areas of security management, performance management, accounting management, configuration management and fault management. Subscriber behavior and attitudes with regards to service provisioning, administration, operation and maintenance could be managed well using AI learning and predictive techniques in such areas as knowledge or data engineering. Service complexity and introduction or deployment of new services would be simplified by the use of intelligent agents. Dynamic cell sizing and planning through the use of traffic statistics and subscriber behavior could be done using AI based techniques.
2 Structure of IN Networks
IN networks emerged through an evolutionary process from a conventional service-specific environment to a service-independent environment. IN-specific components are required to enhance and improve the network by assisting the rapid creation and the efficient maintenance of services. The Service Creation Enviroment (SCE), the Service Management System (SMS), the Intelligent peripheral (IP), the Adjunct (AD), and the Network Access Point (NAP). The SCE provides design and implementation tools to assist in the creation and customizing of services in the SCP. The SMS is a database management system used to manage the master database that controls the IN customer services (eg. Database maintenance, backup & recovery, log management, audit trails e.t.c.) . The IP connects to one or more SSPs , is application-independent and supports generic services for more than one application. Services such as tone generation, voice recognition, playback, compression, call control, DTMF detection and generation are some of the IP services. The AD is configured for one (or few) services and is connected to high-speed links in order to support user requests that need a fast response apart from performing the same operations as an SCP. The NAP is a switch that has no IN functions, is connected to an SSP, interfaces to trunks with SS7 messages or frequency tones. The NAP may route the call to its SSP or IN services. (see FIG.1)
3 SS7 Support of the IN
The elements of IN network rest on the Signaling System No.7 (SS7) architecture. The Service Switching Point (SSP) receives the SS7 signals from the customer and perform call processing on behalf of the user. SSPs serve as the source and destination for SS7 messages by initiating and receiving SS7 messages either via another SSP or a Signalling Transfer Point (STP). The STPs perform translation and routing of SS7 messages between network nodes and databases. They are basically switches that relay messages between SSPs, STPs and Service Control Points (SCPs). The SCPs contain software and databases for the management of calls. They receive traffic (typically requests for information) from SSPs via STPs and return responses (via STPs) based on the query.

FIG. 1
where:
IP = Intelligent Peripheral
NAP = Network Access Point
SCE = Service Creation Enviroment
SCP = Service Control Point
SMS = Service Management System
SN = Service node
SSP = Service Switching Point
AD = Adjunct
4 The IN Conceptual Model
4.1 The Service Plane
This plane describes and stocks the services that are supported by an IN. The first step in building an Intelligent Network is to identify and explain a set of services for the customer. Service features and a set of Service Independent Blocks (SIBs) are next identified. It should be noted that IN is service independent and standardises the procedures and protocols to bring in IN services to a network. In this plane a service may be customised with regards to customer requirements and for a specific commercial use. A Service Feature (SF) can be used with more than one service and must have only one point of control. (see FIG. 2)
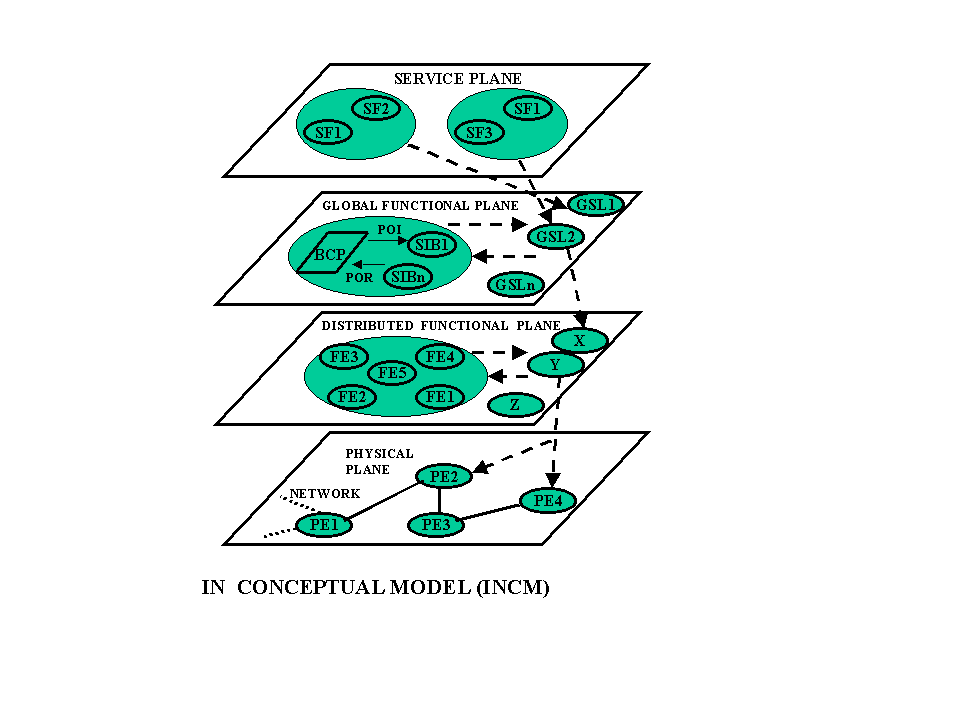
FIG. 2
4.2 The Global Functional Plane
This plane is composed of programs and instructions that are called Service Independent Blocks (SIBs) . It defines the Global Service Logic (GSL) and the interfaces between the GSL and the Basic Call Process (BCP). The order of execution of the instructions in the IN is stipulated by the GSL (i.e. the order of invocation of the SIBs). The interface of BCP and GSL SIBs is through Point of Initiation (POI), the point where the BCP operations are suspended, and Point Of Return (POR), the point where suspended operations are resumed. This interface is modeled on a Remote Procedure Call (RPC) architecture.
4.3 The Distributed Functional Plane
The distributed functional plane consists of a set of objects called fuctional entities (FEs). These Fes pertain to service control,switching, service management, and triggering of events in the intelligent network. The FEs are organised into three broad categories: basic call handling functions, service execution functions, and service management functions. The traffic flow between the Fes can be grouped as:
basic call handling functions: It is divided into the Call Control Agent Function (CCAF) and the Connection Control Function (CCF). The CCF is responsible for basic call processing operations while the CCAF is the interface into the user device. The CCAF interfaces into the CCF and they represent specific elements within a network, such the telephone network or an ISDN.
service execution functions: Organised around the Service Switching Function (SSF),the Service Control Function (SCF), the Service Data Function (SDF), and Specialised Resource Function (SRF). The SSF provides switching functions to the SCF, and the SCF in turn controls the resources at the switch or an intelligent peripheral. The SDF supports the service data (eg. Customer and internal network data) allowing the SCF to access this data whenever necessary. The SRF provides additional support operations for managing intelligent peripherals (eg. Playing announcements, information collection and analysis functions). The Service Management Access Function (SMAF) and the Service Creation Enviroment (SCE) are components of the System Management Function (SMF). Operations of SMF include the introduction and provisioning, and maintenance of services. The SMAF is responsible for providing a MAN-machine interface to the SMF, thus creating an interface to the SMF. The SCEF is used for testing the specifications of the IN services.
4.4 The Physical Plane
It describes the placement of the FEs in the physical components of the network and the interfaces among the FEs such as : Service Switching Point (SSP), Service Control Point (SCP), Service Data Point (SDP), Intelligent Peripheral (IP),Adjunct (AD),Service Node (SN), Service Management Point (SMP),Service Management Agent Point (SMAP),and Service Creation Enviroment Point (SCEP). The physical layer also describes IN in relation to layer 7 of the OSI Model, including the Application Process (AP), and the Application Entity (AE).
4.5 Functional and Physical Entities
Call Control Access Function (CAF): Allows user to access the CCF; handles call setup,termination.hold-on,etc., can also provide user with CLASS (Customer Local Area Signalling Services). This function is found in the SSP and NAP.
Call Control Function (CCF): Supports establishment of conventional bearer services. This function is found in the SSP.
Service Switching Function (SSF): Recognizes calls requiring IN service processing. Interacts with call processing and service logic. Function resides in the SSP.
Service Control Function (SCF): Furnishes control for a call requiring IN service and handles service-related processing activities. Function resides in the SCP, AD and SN.
Service Data Function (SDF): Supports access to network data and provides a logical view of the data to the SCF. Function resides in the SCP,AD and SN.
Specialised Resource Function (SRF): Supports user interaction with the IN resources through interaction with resources such as DTMF, voice recognition and announcements. Function resides in the SN and IP.
Service Management Function (SMF): Allows access to IN resources for the transfer of information. Function resides in SMS.
Service Creation Environment Function Deals with the creation, validation, and evaluation of new
(SCEF): IN services
5 IN Services Objectives and Goals
5.1 Service Definition
The mobile user of today no longer accepts his services being dictated to him or her. He or she expects a variety of services to be offered by various providers and for these services to be flexible enough to meet the individual demands. AI would play a vital role to guarantee the flexibility required with less complexity as compared to existing conventional methods. The user does not care that there may be a contradiction between the requirements for an individual personal profile and the needs of the mass market. The user also expects a rapid if not immediate deployment of services from the moment of request. Using the unsupervised learning technology of intelligent agent creation and modification, service deployment would be faster and completely under user control.
In mobile systems like GSM but also in ISDN, the user has already a broad choice of services, in particular supplementary services. This variety of services has led to complex instructions on how to use these services. Ordinary users will not accept an increase in complexity of service handling. On the contrary, they will prefer a simpler ‘personal assistant type’ man-machine interface. Service handling simplicity can be easily archieved using ‘AI-based personal assistants’.
5.2 Service Provisioning Roles and Relationships
Third Generation systems would consist of the following traditional but well developed roles in most models: Network Operator, Service Provider, Subscriber and User. However, the emerging new business environment would create new classes of players such as Value Added Service Providers, Content Providers, Service Brokers and others. (see FIG. 3)
Such roles would produce various relationships between the different classes. One to one or one to many relations would be possible. A unique and simple model is needed that would be referred to for standardisation processes.

FIG. 3
3G scenarios would witness Customers subscribing to services at different service providers while maintaining a single identity. Service providers may offer both services and technical support to more than one network operator. From the user’s perspective the term "Home environment" would be adopted.
For a prosperous business in a competitive environment, a service provider is obliged to offer products which meet the users' expectations better than the products of his competitors. He needs the technical means for creation of such products using AI-based agents which would not only simplify the service creation process but would also increase the speed of service deployment. Present IN concepts offers some components for flexible service offerings but more capabilities are needed.
6 Markets and the Evolution from 2G to 3G Networks
The strong regulatory support and commitment of operators in various parts of the world which facilitated the development of 2G systems is fading quickly. The challenges and risks inherent in developing a completely new system seem to be too high today for any manufacturer or even commercial groupings.
The modular concept for 3G systems requires a phased implementation strategy. Such modules can then be developed and implemented in compliance with market demands and AI-based interworking service functions would be vital for an easier and gradual emergence of Third Generation services. The design of a radio access part/interface for the provision of global multimedia services in a GSM environment could serve as an example. According to market forecasts such services are needed very soon by the market and technical concepts are already advocated for its technical implementation.
In subsequent 3G phases, more 3G modules will be combined with the 2G technology until a stage is reached in which only 3G components work together forming in this way a fully deployed 3G system. The modular concept and its phased implementation may seem to have shortcomings ,compared with an optimum solution, but compensation in the form of reduced economic risks and early return of investment would be an important advantage.
High bit-rate service may have limited coverage at least in the initial implementation phase of 3G networks. In order to provide continuity of services especially in the early days of the Third Generation it is necessary to support a seamless handover between UMTS and GSM (including GPRS) and vice versa. 3G services should be supported in residential, public and office environments and in areas of diverse population densities.
An adaptive means using the fast developing AI-agent technology should exist for informing 3G roamers of any limitation in service capabilities he may wish to use, if more than one 3G radio interface is provided to roaming users in a given area. High-end terminals in 3G systems must adapt to the respective radio interface and access appropriate service capabilities.
7 3G Value-Added Service Provision Objectives
3G systems shall have standardised service capabilities required to build 3G services as exemplified later in the document. Common features in the provision of 3G services would be:
Flexible service definition;
Personal mobility in mobile and fixed networks;
Support for multi system terminals;
Support of multi mode operation;
Capability for international roaming and internetwork roaming;
Flexible charging, including pre-payment and electronic purse systems;
Comprehensive real time charging information to the user;
Integrated mailbox-service for voice, fax, text and other formats (in mobile and fixed networks)
Personal Assistant and intelligent agent support;
New multimedia and on-line services access;
For call-type communication: flexible call routeing (screening, barring, forwarding) with a comprehensive interface across different networks.
One-stop shopping with a single contract for the provision of a multitude of services will be the dominating scenario.
8 Service Categories
Basic services provided in 3G networks are audio, video, facsimile transfer, data communication, Internet services, especially Web-Browsing, e-mail/voice mail, paging, messaging, and combinations of these i.e. multimedia. 3G service capabilities for these services should take account of their discontinuous and asymmetric nature in order to make efficient use of network resources. Supplementary services are generally not standardised and they are defined by service providers or other entitled players based on service capabilities as a common platform.
Speech conversation in 3G systems must be of high quality. Codec solutions are required for both lower or higher bit rates. The Adaptive Multi-Rate (AMR) codec could be the basic speech codec for the Third Generation. Real- time or near real-time video ,as already used in the internet, would be possible probably with the emergence of Wideband CDMA over the air interface. Traffic density for video communications is assumed to increase significantly in 3G networks just a few years after implementation.
3G Multimedia services and service capability would depend on the following:
mobility services which would be related to the mobility of the user, like location identification services; conference services with bi-directional and synchronised real-time transfer of voice and moving pictures; conversation services which allow bi-directional dialogue communication with real-time end-to-end information transfer; distribution services which provide continuous flow of information from a central source; retrieval services which allow to retrieve information from one source at a time; collection services which allow to retrieve information from several sources in parallel and message services which offer user-to-user communications with store-and-forward capabilities
9 3G Standardised Service Provisioning Capabilities
One of the main criteria distinguishing 2G and 3G system can be summarised as "mass service for individuals". This requires new concepts for service provision including service creation, service operation and service management in a phased approach.
3G Service Creation mechanism would be standardised and would allow flexible and immediate reaction to market requirements. The process of service creation comprises service specification, service definition, service implementation and service verification. Service Operation in 3G networks would allow for complete service portability and easy service handling. Operational mechanisms would include service access (identification, authentication,..), service compilation, service execution, service control and the generation of billing records should cater for different users, service providers and network operators. Mechanisms are also required for service administration, service monitoring, service supervision and service provider billing.
Due to the number of possible individual service profiles, user-friendly and flexible AI methods are required for service administration in order to store and verify the user service profile parameters using distributed databases with a hierarchical access for the user, the subscriber, service provider and network operator. Service Portability in the form of roaming between different 3G environments shall be possible without limiting the user in his personal service set and accustomed user-interface but may be limited only by physical constraints.
10 The VHE Concept
Virtual Home Environment
(VHE) is a system concept for service portability in the Third Generation across network borders. It should work under the ‘mass services for individuals’ condition. In this concept, the serving network emulates for a particular user the behaviour of his home environment. For the user, adaptation of his service handling is therefore unnecessary.The concept of VHE has been proposed as the technical basis for simplification of service handling at the user’s side and for service profile portability across network borders. When using the appropriate multimode or flexible terminals, users may then roam between 2G and 3G networks without any additional requirement for backward compatibility.
The term VHE was chosen to reflect the communicating users’ view. However, the term includes all elements for the realisation of the concept (VHE Services Platform). When applying VHE technology, the serving network requests from a roaming user some basic information such as the name of the service provider. This information is used to check acceptance against the list of roaming partners and to perform authentication according to the principles of the home environment. Assuming positive outcome of these two steps, the serving network may request further detailed information on e.g. the service profile of the respective user, the used codecs and the MMI he is accustomed to. AI-based syatems may further simplify the VHE concept by interrogating the "Home enviroment" databases and decide on the profile,codes and MMI appropriate for the roamer. (see FIG. 4.)
VHE realisation requires secure and standardised links and interfaces, certified software-modules and software plug-ins, robust, reliable and cost efficient transmission and storage, modular terminals, an open terminal operating system and efficient USIM capabilities.
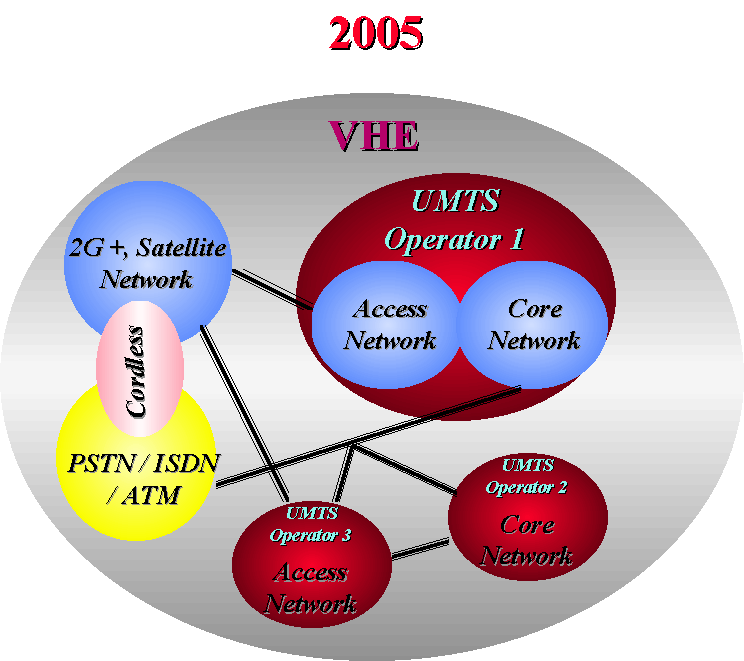
FIG. 4.
VHE service provisioning requires various mechanisms like service emulation, service remote execution and service enabling.
The Service Emulation function is one method for the information transfer of user specific information and involves the downloading, e.g. in form of objects, from the services provider’s service node to the serving node of the serving network. Objects might be introduced to the User's Personal Identification Card (USIM) or the terminal where they are stored. With this information available, the serving network can now emulate the behaviour of the home environment to the necessary extent.
The Service Remote Execution (‘service tunnelling’) function gives the subscriber the possibility to use his own VHE services although the serving network might not be able to support the desired service or the storage and execution of the appropriate data. For example, when using some of the 2nd Generation systems for the access of 3G services. Mechanisms for the provision of a transparent transfer of the relevant service data are necessary.
The Service Enabling function covers cases where certain services will be made available in the serving environment although not foreseen in the subscribers original VHE profile. Basic mechanisms of the service emulation and the remote service execution apply, but additionally needs are for flexible charging capabilities and mechanisms for online subscriptions to value added services (VAS) e.g. via Trusted Third Party, electronic purse (e-cash,...) or online VASP subscription. Flexible Air Interface ( software defined radio) would allow service provision when roaming outside the home environment and would be largely facilitated by use of mobile terminals with flexible e.g. programmable air interface, covering a wide range of variation in 3G networks. It is vital for the Third Generation internal evolution to higher performance and will also facilitate roaming between 3G and pre-3G networks such as GSM.,
11.1 Technological Integration
The designing process of a 3G mobile system has to take into account of the latest achievements in modern technologies. Some examples of technological intergration consist of the convergence of communication, information and entertainment technologies, the emergence of unclear distinction between fixed and mobile network concepts , multimedia presentation, transfer of application support software packages (e.g. Java applets), software controllable terminals, high-capacity chips and memories. (see FIG. 5)
The future 3G UMTS will be able to provide data, video (still and moving pictures) and voice, through the convergence of fixed, mobile and satellite networks. This process will be market-driven ,and not technology-driven. The 3G market would probably be looking for:
One Number
One Bill
One Stop Shopping
One Customer Care
Seamless access to the same services independent of the type of access and complete integration of fixed, mobile and satellite networks would result in cost reduction due to new infrastructural consortia and alliances between Operators and Service Providers, which would use existing distributed infrastructures, improving the already existing services and immediately offering the access capability to the new technologies for building up a real and a virtual powerful network.

FIG. 5
The UMTS is a solution which will take the personal mobile communication from the Second to the Third Generation as a natural evolution based on different technologies and may be the basis for a multimedia mobile information. This solution and flexibility should guarantee backward compatibility on the fixed, mobile and satellite networks of the 2nd and 3rd Generations. The Satellite Network Operators would eventually have similar infrastructures as those of Celluar Network Operators, based on ATM-like advanced technologies and cellular-like architectures (IRIDIUM, GLOBALSTAR, ICO, ...) and integration would probably progress as shown below:

FIG. 6
On the other hand Mobile Network Operators would probably achieve Mobile-Fixed Network Integration towards UMTS as shown below:

FIG. 7
11.2 The Internet and E-commerce
The use of Internet services is already very common and well accepted by the user. The 3G system has to take into account the achievements and also the requirements of Internet and intranet services, in particular Web-Browsing, including all possible applications and the commercial aspects, which put high demands on bandwidth requirements, and the conceptual elements used in the provision of Internet services.
E-commerce is already operational via the internet and the near future would witness the use of mobile phones to carry out transactions like money transfers between various accounts in such areas as shops and holiday resorts. Short message services would be used to send account balances to customers as well as special promotional announcements on new products or services, sales, discounts and personalised customer services such as greetings of special customers by name and birthday announcements. Already there are announcements of Internet-based mobile phones (Web-phones) to be released on the market by the end of 1999, which allow users to surf the Internet and read news or e-mail. These Web mobiles achieve cyber-accessibility using a software Wireless Application Protocol (WAP) which adjusts Internet sites to the phone and give services such as online banking, cinema and airline ticket booking or restaurant reservations. Artificial Intelligence systems could be used to study the profiles of various customers and learn their shopping habits and tastes. Such AI databases could then be used by predictive programs to advise on the factors affecting customer churn.
11.3 Advanced SIM Cards and Mobile Terminals
The future SIM Cards would have attractive features like an ISO size SIM Card (full size); More memory available, for multiple information storage; Multidirectory SIM Card for Multiple applications (TLC and others roaming from one device, cellular phone, to another device) like an ATM reader; Dual Chip for remote connection (regular contact chip) and local connection (contactless chip) for such things as Credit/Debit Card transactions.
The role of the SIM Cards in the evolutionary phase between the 2G and 3G Systems can be shared in three parts: As a bridge between the Network and the Terminal , it would be up to Terminal and SIM Card Manufactures to consider an optimised use of the memory of both devices. (see FIG. 8)
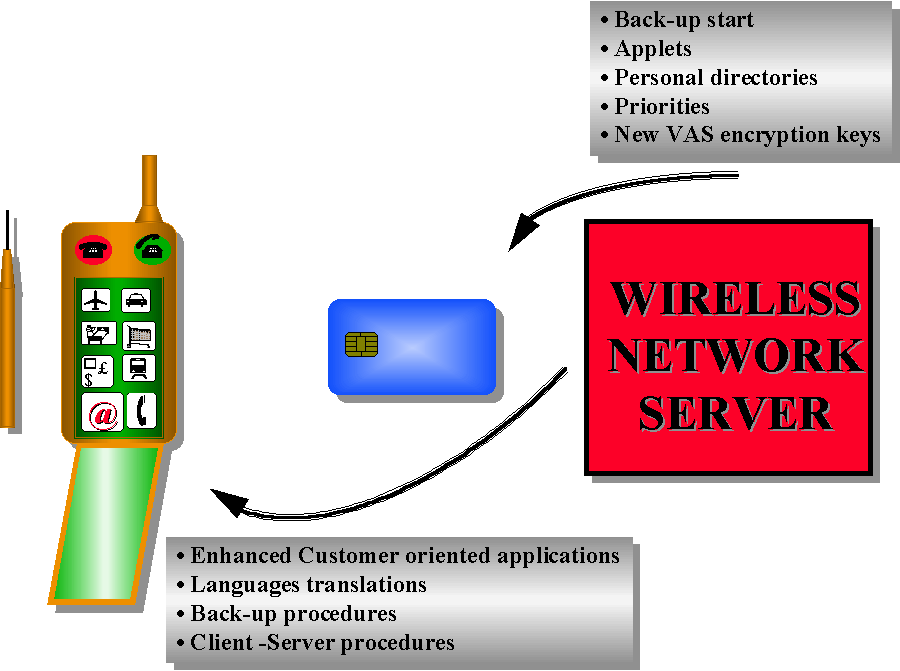
FIG. 8
What would probably require clarification is whether the terminal and the SIM Card will have locked Applications between them for security reasons. The SIM card is strategically vital because it could be used to provide new Value-Added Services for customer retention
FIG. 9
The new SIM Card has to be technology independent to provide seamless services.

FIG 10
The capabilities of the 3G Universal Subscriber Identity Module, USIM will be extended compared to today’s SIMs with such things like the storage of personal profiles for services or MMI, storage of service logic and support of multiple registrations. A very good level of security is to be guaranteed, e.g. the protection against misuse and the authentication of user-to-USIM, USIM-to-network and network-to-USIM. It should be possible to be registered on multiple terminals with the same subscription from the same subscription provider, but different services, at the same time. It might also be possible for the Third Generation subscriber to use certain services without the USIM being physically present in the terminal, e.g. for services that are free of charge or where the user and the network does not require authentication or ciphering.
The evolution of the mobile terminal technology will depend more on Information Technology than Radio Technology. 3G systems would offer services which will make mobile communications part of the user lifestyle with an integration of business, leisure services, including information , travel and multimedia communications. The predominant role of the USIM Card would make the loss of the terminal inconsequential to the user because a new terminal could be supplied to the user rapidly and reloaded with the customer’s VHE.
Features likely to be found on 3G Mobile Terminals would include Modularity in both hardware and software, Software Oriented Radio to adapt any radio interface, Terminal Operating Environment (TOE) with Radio Function, Terminal function and Service function, Intelligent Power Management for optimum battery life achievable by the terminal with charging techniques like solar, kinetic and piezo-electric and New Man-Machine Interface requirements to support the terminal aspects of the VHE and the personalisation of the services. The MMI to the mobile could allow a number of different user interfaces such as: polymer bending screens, keypad, colour displays, voice activation, holography, virtual environment interface (which is fundamental for the creation of a virtual wide screen),written input, touch sensitive displays, language translation, brail-to-text, voice-to-text for deaf and deafmute, new authentication methods (electronic signature, voice recognition, finger-print, retina-print). A Standard Accessories Interface terminal would be able to communicate directly with any device with standardised connection points and compatible communication protocols. Exchangeable keypad environment would allow MMI alteration which would be user-driven and dependent on the application. SIM/USIM full compatibility would be a requirement for 3G mobiles. Security would be required for stored information about the user for transaction applications, medical details and protection against fraudulent access. Recyclable Material would be important in line with the concept of inconsequential terminal as well as Advanced Health and Safety Capabilities.
11.4 The ATM,VLSI and WCDMA Revolutions
The emergence of Asynchronous Transfer Mode (ATM) implies that various services with differing bandwidth requirements can be served with the same high speed network. Future IN services would include anything from Video, images, facsimile, data and voice which would then require the same service provisioning facilities, the same bearer network and the same subscriber apparatus. This means that Future IN services would depend on all related facets of technological developments. The increased volume of transactions for processing need high speed VLSI processors. The demand for high bandwidth by bandwidth-hungry services like realtime video means that better physical transmission media like optical fibres and Waveband Code Division Multiple Access radio is required to handle the increased bit rate. Future mobile phones and accessories would naturally be small and compact video computers which would be able to handle all these bandwidth on-demand services.
11.5 Service Building & Management
Complex service introduction and deployment would be easier to achieve using Intelligent Agents.
ServiceBuilder, a product developed by Nortel, would provide rapid deployment of services with products based on the international standards from ITU-T and Bellcore. The system adheres to Capability Set 1/Refined (CS-1/R) ,operates with IS-41 and SS7 and will evolve to the support of Bellcore’s AIN 0.2 Call Model.
ServiceBuilder provides IN services such as number translation, virtual private networks (VPNs), location of personal communications services (POS) users, credit card services such as Automated Calling Card Services and also Prepaid phone calls.
AI-assisted service building and management is possible if one looks at the architecture of the ServiceBuilder which consist of SIB libraries of C++ code and application programming interfaces (APIs). The Service Logic Execution Enviroment (SLEE) is an entity which allows the service provider to tailor services in a more flexible manner than traditional service creation operations. It is this entity which would then interact with an AI-based agent to learn and process queries on service creation
11.6 Object-Oriented Finite State Machine Modeling
IN concepts have evolved to satisfy more demanding and sophisticated requirements of the user and in parallel with these increased needs are technological advances such as high bandwidth circuits, fast processors and object_oriented programming. Intelligent networks use object-oriented finite state machine modelling and the Common Object Request Broker Architecture (CORBA) is used to define how objects interact in a distributed enviroment. This concept models a system with a boundary on a finite set of states in which the system can operate as well as a finite state of transitions that are possible from one state to another. The advantage of using Finite State Machine Modelling is that it imposes an unambiguous and strict set of rules on the behavior of the software, if the input to the software is known. Object-oriented techniques are a valuable tool to describe a system and characterize the states of that system. The system is characterized by objects and these objects represent properties of the system. Each object is described by its unique characteristics (or attributes) as well as the actions permitted to manipulate the objects (or functions). IN design philosophy the need of atomic actions requires the objects to be self-contained, modular processes which can be easily combined to form IN operations. Object-oriented FSM provides descriptive modular objects, supports a vendor-independent system to describe IN functions. An example is a view of an SSF to an SCF, information flow definition between the SSF and the SCF, and verification of the correct sequencing of functions within an SSF.
11.7 Common Object Request Broker Architecture (CORBA)
The Common Object Request Broker Architecture (CORBA) is a standardized procedure for defining how objects interact in a distributed environment, based on a client-server model. The basic idea is to make an application independent of language, hardware and operating system platforms on which an object operates. A client issues a request for a service without concern about these dependencies. The CORBA architecture consists of the Object Requester Broker (ORB), Invocation interfaces, base object interfaces and interface repository. Interfaces are executed with the Interface Definition Language (IDL), a compiler-independent programming language, which is used to specify client application interface to objects. Clients make requests for services from objects. The interface repository is a database of definitions needed for applications while the server objects satisfy client request. Client applications in IN systems could be AI-based programs which would then sent requests to knowledge or rule-based databases and process queries during the inference stage or rule or knowledge updating during the learning phase. One could then think of a distributed AI-based program. (see FIG. 11 and FIG. 12)
12 Telecommunications Management Network (TMN)
TMN is organised around OSI and object-oriented techniques which makes it supportive of Common Management Information Protocol (CMIP) and Common Management Information Service Element (CMISE). The objectives of TMN are to provide a framework (a generic model) for management,
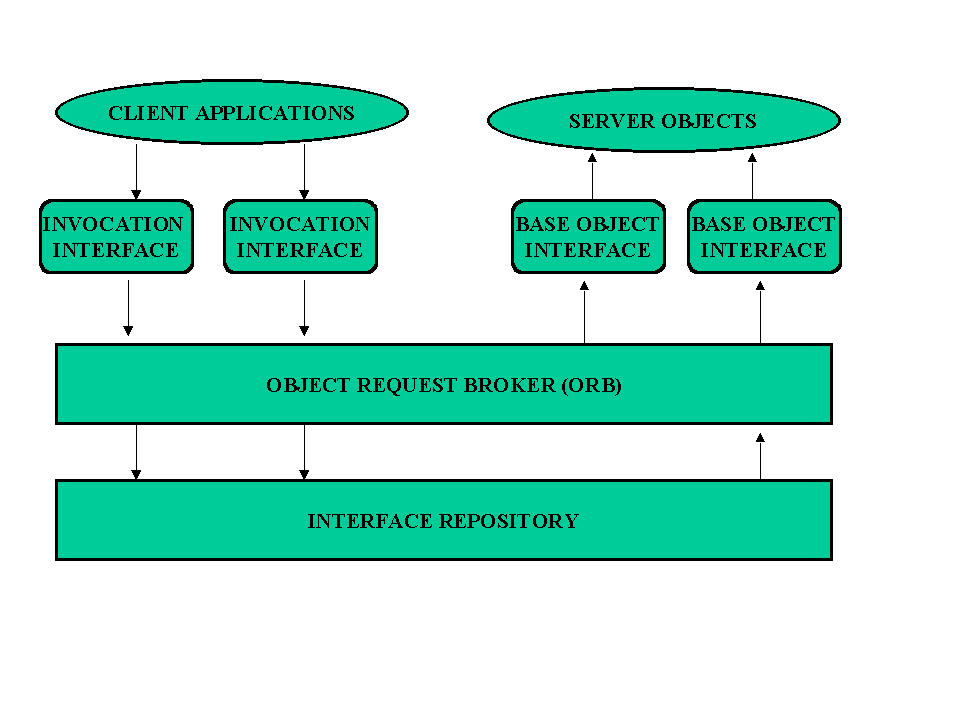
FIG. 11
FIG. 12
description of the appropriate functions that exist in the parts of the TMN, definition of the interfaces between the TMN and the actual networks, usage of OSI-based services, employment of the object-oriented approach to represent TMN architecture and to employ the OSI five management functional areas (X.700).
Intelligent Network TMN would be shown as expert driven (knowledge-based or rule-based) and pattern analysis-based in reference to its five management functional areas of security management, performance management, accounting management, configuration management and fault management. The use of AI-based Automatic Test Systems would result in better fault diagnosis and detection in an IN network in fault management. In security management, learning certain features of subsribers such as voices signatures, finger prints, facial images and other behaviors ,the IN would ensure that each subscriber would use only those services which have been allocated to him/her. This highlights the role of other technological developments and the AI’s dependency on such areas like voice-recognition, and image processing. AI-assisted configuration management would include such things as Network Traffic Management whereby control of network congestion is carried out by reconfiguring the network or Automatic Cross Connection of a digital private circuit via a 2 Mbit/s channel over the transmission bearer. Configuration management would be a key automated business activity to control changes to the configuration of the network (i.e. hardware, software and data). Such changes must be carried out in a manner that protects the integrity and security of the network. The cost of failure can be very high and can result in loss of service to an exchange. A large number of configuration systems have evolved over the years and it is therefore necessary to develop AI-based generic processes and network configuration systems within the network management architecture to create future manageable automation of this task. An AI-based system would work out the assignment details and determines the changes and trigger the production of work scripts which can be forwarded to implementation programs automatically. Such processes can be initiated by other processes like network planning to introduce new capacity or changes to its structure or usage processes for new service provisioning or performance and fault management processes to replace faulty equipment. Data and software update changes are converted into the appropriate machine interface before verification, archiving and loading into the network.
Interworking TMN functions use the conventional manager/agent concept for the exchange of messages. The manager issues management messages and receives notifications, and the agent manages the managed objects, receives messages (directions) from the manager, and emits notifications to the manager. CMIP is the layer 7 network management protocol that is used to exchange the network management messages between the manager and agent. CMISE is the OSI-based service definition that defines the interface between the CMIP software and the manager/agent software. The Management Information Base (MIB) is an important part of TMN and identifies the network elements (managed objects). It also contains the unambiguous names that are to be associated with each managed object. Since the MIB is a database that contains information about the managed objects (e.g. number of packets sent or received) it can therefore act as input information for queries that drive AI-based Managers or Agents which then exchange information through network management protocols, such as CMIP.
TMN provides a model that is supportive of and complimentary to IN , but the future IN would see a likely integration of functions and objects since AI-based components would be distributed across the networks. Intelligent network architecture would be based on reusable and common software programs with CORBA and object-oriented MIBs being valuable tools to manage the IN system components.
13 Service Provisioning
Subscriber Behaviour and Attitudes are usually related to culture and population behaviours and have direct bearing on how you provide service. Subscribers have different profiles of behaviours due to different socio-economic groupings. Since subscribers are increasingly demanding customer-specific services and no longer require the situation where services are dictated to them but instead require various services and flexibility. Self-provisioning would be easily achieved with the assistance of AI. For example subscribers would have elastic mailboxes (voice, fax, image, etc) whose size for a given period of time would depend on the frequency and length of the messages. This would result in subscribers having different mail boxes and is an excellent example of the use of AI in dynamic resource allocation. Techniques which have been developed in a particular branch of Artificial intelligence called knowledge or data engineering can be used in predicting customer churn in the competitive cellular environment . Such programs would serve a dual purpose by providing useful marketing information and at the same instant providing as input to self-provisioning programs.
14 Network Planning and Configuration
Dynamic cell planning and sizing is an attractive area for application of AI. Traffic statistics and patterns and other parameters like geographical or man-made profiles can be used as input data for invoking knowledge-based queries on cell-sizing. By learning traffic statistics and mobility patterns a cell-sizing and planning system would have an advantage over the conventional methods because there would be better coverage and allocation of channels with lesser human assistance.
15 Resource Management
By using a learning AI program, resources can be allocated as required and for a specific service for different times. Instead of using human experts to keep track of the capacity of the network for different services using various formulas ,a knowledge-based or rule-based program will learn the adequate capacity required by a specific service, customer group and system. This will then eliminate the use of blanket formulas for the same system over different population groups. Although these conventional methods work very well, the AI-based program fine tunes the process resulting in adequate resource allocation, optimum dimensioning and cutting down an extra cost of investment. In future one would talk of self-configuration networks which learn the capacity of a system for a specific service area.
16 CONCLUSION
The aim of this discussion paper was to present various illustrations of IN network development functions and architectures pointing out how AI would assist in the process.
This survey serves to clarify the inevitable world trend of IN-based mobile communications research and developments and the increasing importance and role of AI to realise these future networks. These third generation IN-based networks would allow efficient deployment and management of new wide-band and multimedia services.
REFERENCES
[1] 3G Service Requirements and Concepts, Version 3.10,28 April 1995. GSM MoU Association Permanent Reference Document: TG.21.
[2] Vision for the Evolution from GSM to UMTS, Version 3.0.0, 30th April 1998. GSM MoU Association Permanent Reference Document: TG.13
[3] The Intelligent Network ,Customizing Telecommunication Networks and Services,Prentice Hall Series 1998
[4] B. Krulwich, "Automating the Internet: Agents as User Surrogates," IEEE Internet Computing, Vol. 1, No. 4, July/Aug. 1997, pp. 34-38
[5] Unmasking Intelligent Agents, IEEE Intelligent Systems & their applications, March/April 1999