TCP/IP an invisible process behind the interconnection
Interconnection:
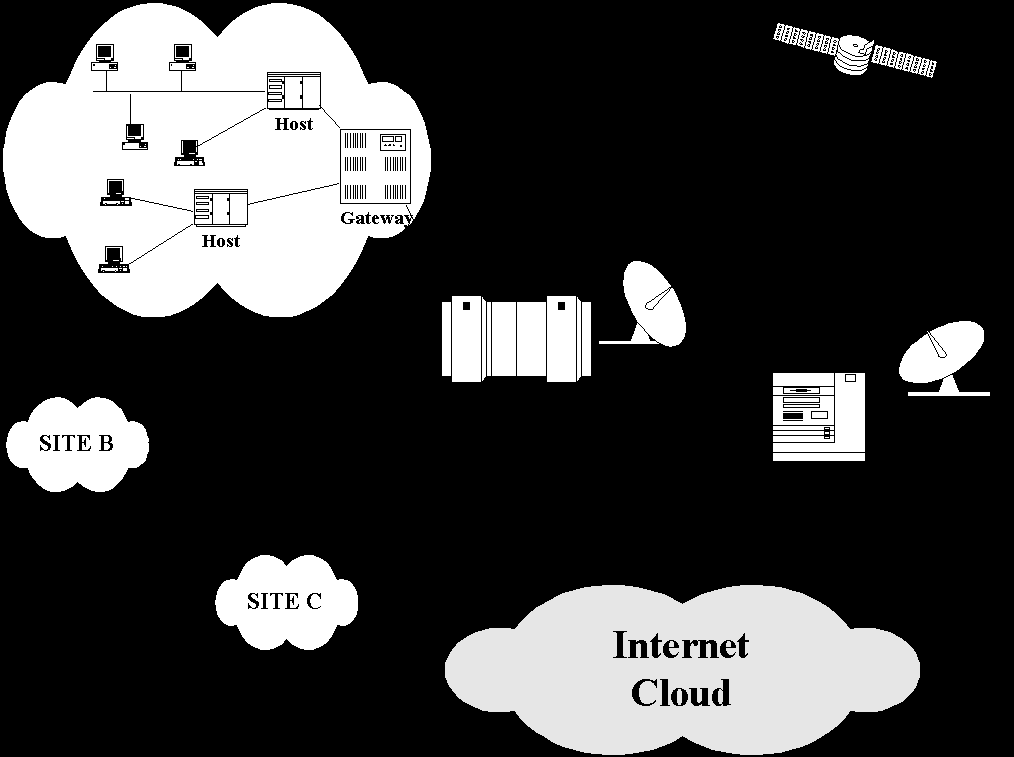
The topic of present day technology is the interconnection of otherwise autonomous networks. There are several motivation for wanting to make such interconnections. Having a single large network may be impractical because of address space limitations, limitation on how much one network management operator can handle, the need to localize the effect of configuration changes, and the existence of non overlapping patterns of ownership and organizational jurisdiction.
The connection may be between homogeneous networks or it may be a heterogeneous interconnection, clearly the least difficult inhomogeneity to handle is one between different release levels of a common product line or different variants of a common designs. However, the big challenge to be met concerns inhomogeneous network interconnections that will require significant protocol conversions across many protocol layers. The mechanism by which the interconnection is affected at the point of contact is gateway, a special node that belongs simultaneously to the two networks. The gateway may be implemented as a machine dedicated to the purpose or it may be special piece of software running in a CPU that is also running user applications.
While discussing computer communications, it is useful to recall that the communication takes place at the request and agreement of processes, i.e. computer program in execution. Processes are the actors in the computer communication environment; processes are the senders and receivers of data. Processes operate in computer or hosts. It should be noted that terminal-host communication can like wise be implemented as interprocess communication.

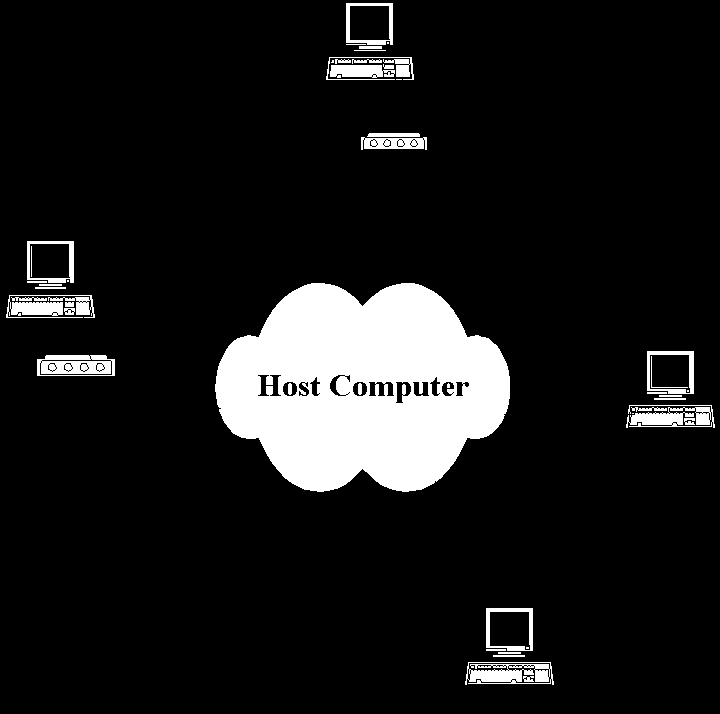
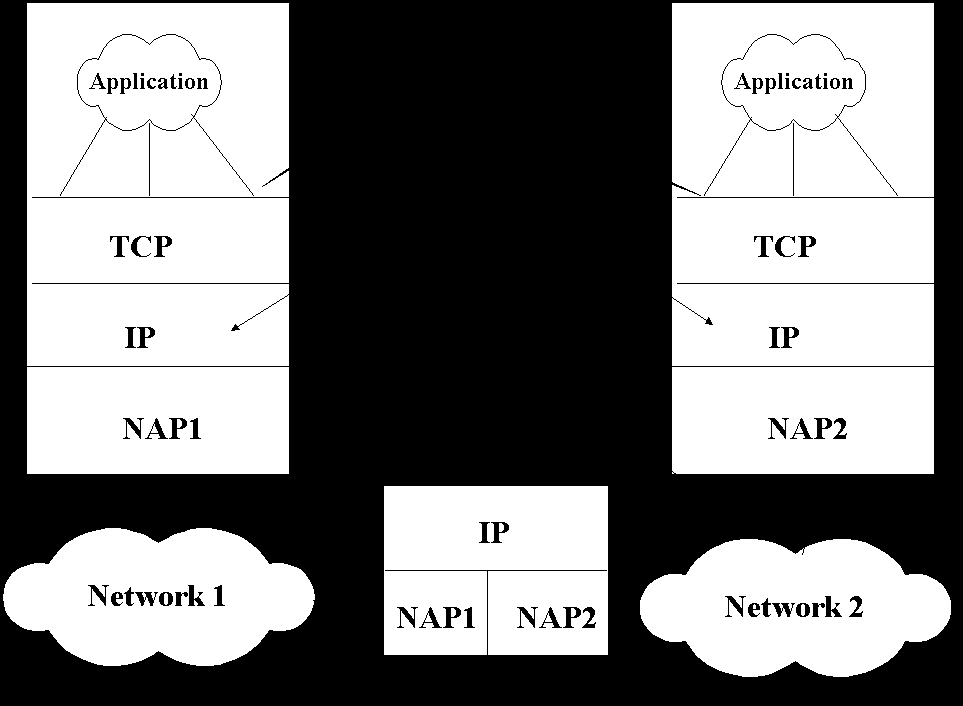
The protocol used in constructing the communication capability provide an interprocess communications system. Fig. 2 shows how the combination of network and the host network interface (hardware and software) can be viewed as providing an interprocess communication system.
When a new host computer is to be connected to an existing network, it must implement the protocol necessary to match the existing protocol used in the network. The new host must join the network wide interprocess communication system so the processes in that host can communicate with process in other hosts in the network.
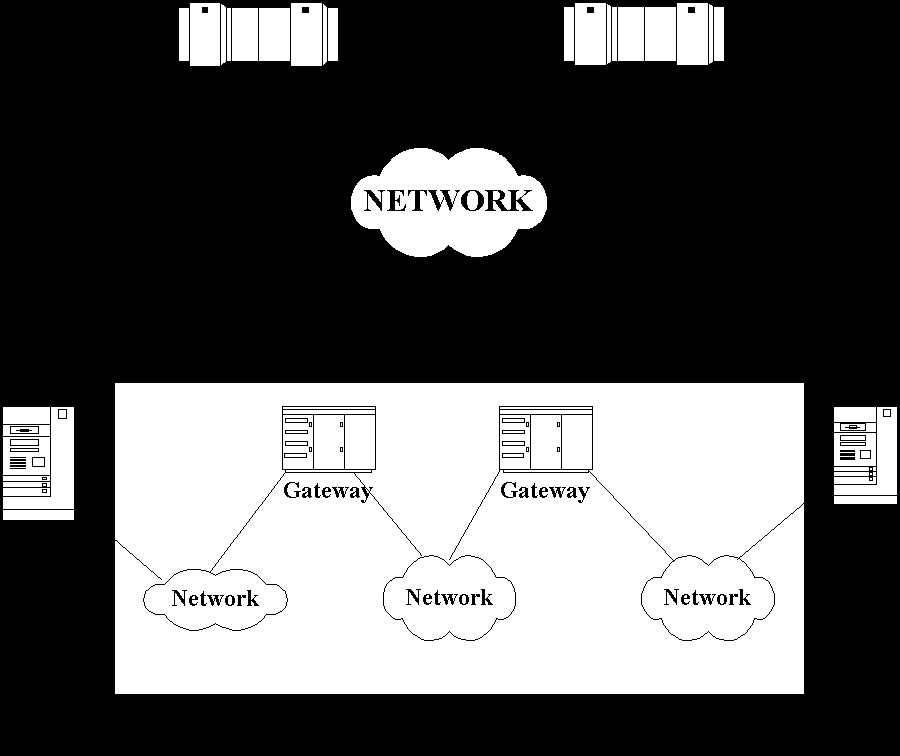
So for we have discussed about the single network. The interconnection of networks require that the process in the hosts of the interconnected networks have a common interprocess communication system. This may be achieved by converting the networks to a new interprocess communication system, by converting one or more levels of protocol to new protocols, or by translating between pairs of interprocess communication system at their point of contact. Two or more networks are connected via a device (or pair of devices) called a gateway. Such a device may appear to each network as simply a host on that network.
Some gateway simply read messages from one network (unwrapping them from that network's packaging), compute a routing function, and send messages into another network (wrapping them in that network's packaging).
Since the networks involved may be implemented using different media such as leased line or radio transmission, this type of gateway is called a media-conversion gateway. Other gateways may translate the protocol used in one network to that used in another network by replacing messages received from first network with different messages having the same protocol semantics but with the syntax of second network. This type of gateway is called a protocol translation gateway.
It should be clear that the distinction between media conversion and protocol translation is one of degree: the media-conversion gateways bridge the gap between differing network and higher level protocols while protocol translation gateways bridge the gap between differing network and higher level protocols.
There are several issues in the translation approach to network interconnection.
. At lower level protocol translation cause no problem because physical level and link levels are hop-by-hop in nature. It should be noted, though that different protocols even at these low levels may have impact on the reliability, throughput, and delay characteristic of the total communication system.
. At the network and transport levels, the issue of message size, addressing, and flow control become critical. Unless one requires that only message that can be transmitted on the network with smallest maximum message size be sent, one must provide for the fragmentation and reassembly of message (breaking the message and rejoining at the destination). fragmentation and reassembly is the division of long message into parts for transmission through a small message size network, and reconstruction of these parts into the original message at the destination.
Thus the key protocol mechanism are
* Segmentation and reassembly
* Encapsulation - Addition of control information to data
* Addressing
The ARPA sponsored research on interconnection of network that led to a two-level protocol to support the above services. The ARPA sponsored work on networks has developed an Internet Protocol (IP) and Transmission Control Protocol (TCP). TCP is a logical connection transport protocol and is a level 4 in OSI model of protocol structure. The IP is datagram (the data are transferred without the prior mutual construction of a connection). IP is the network protocol of the internet (collection of interconnected networks). The actual networks used are of various kinds (e.g. the ARPAnet, radio network, satellite networks and ring or cable networks) and are referred to as local networks even though they may span continent or oceans. The interface to local network is a Local Network Protocol (LNP) e.g. MAC/LLC in Ethernet LAN. In ARPA mode, the networks interconnect via a single device called a gateway. A gateway is a host on two or more networks
Each network address a gateway on it in the same way it addresses any other host on it. The information require to deliver a message to a destination in the internet is carried in the IP header. The IP is implemented in the gateways and in hosts. A sending host prepares a datagram (IP header + original message) and then selects a gateway in its own net to forward the datagram. The sending host then sends the datagram wrapped in a local network packet to that gateway. A gateway receives a packet from one of the local networks to which it is attached and unwraps the IP datagram. The gateway then examines the IP header and determines the next gateway (or destination host) address in one of the local networks it is directly connected to. The gateway then sends the datagram with the IP header in a new local net packet to that gateway (or host).
IP has no provision for flow control or error control on the data portion of the message. There are no acknowledgements of IP messages. The IP is simple and the gateway may be implemented in small machines. Thus TCP uses end-to-end mechanism to ensure reliable ordered delivery of data over a logical connection. It uses flow control, positive acknowledge with time out and retransmission, sequence number etc. to achieve these goals. ARPA has used these techniques to interconnect several very different networks including ARPAnet packet radio nets, a satellite net and several local networks.
Thus TCP/IP protocol suite architecture is based on a view of communication that involves three agents: process, hosts and networks. Processes are fundamental entities that communicate which execute on hosts.
Interconnection is about delivery. The requirement for open systems arose because people wanted complete freedom to communicate with each other without worrying about the systems, distances or technicalities involved; just as telephone user of today excepts to be able to make a call from anywhere in the other country, using consistent dialling codes and oblivious of whether the voice is travelling over land, under sea or via the air waves. The objective of an open system is to allow data to move transparently. In other words, data moves in the same way regardless of where it is going, where it comes from, who sent it, who needs it or by what actual physical medium or media (copper, glass, microwave, satellite or so on) it travels from its source to its destination. As with postal delivery system, you post a letter of any size, shape and weight to any address and do not need to concern yourself at all as to how it it actually delivered, as long as it gets there on time. You can ofcourse pay more for a better or guranteed service exactly as you can in an OSI network.
The concept of OSI:
If you drive a skewer through an onion it passes through the layers of the onion on the way in and then, on reaching the centre, passes through the same layers but in the reverse order. In a communication context, the layers of the onion are analogous to a logical sequence of functions which must be carried out in order to construct and transmit a message. The last function to be performed before the message can be transmitted over the physical network (the centre of the onion is conversion of the data into electrical signals, light pulses, sound waves or whatever form is appropriate to the physical medium forming the network - be it a ether, wire glass fiber or water. At the receiving end the message goes through the same process again - thus time in reverse order, starting with converting the network signal into data.
Interworking begins when the groups eliminate duplication of effort by drawing upon the resources of the others, improving efficiency and productivity. The connection of neghbouring LAN spans to widely dispersed workgroups and finally the overall enterprise. The enterprise network may stretch around the globe, connecting corporation’s internal operations, customers, and suppliers. The devices that feed traffic to networks fall in categories of repeater, bridges, routers and gateway.
Repeater, bridges, routers and gateways all interconnect networks, and to various degrees their functions overlap. So the choice of interconnect device may not be clear. Their proper use requires delving into layer functions of the OSI reference model. In this communication model, every layer has its own set of protocols that provide a set of services to the adjacent layers. The reference model consist of suite of communications protocols at each layer that perform the mayriad tasks required by communications environment. A layer on one device communicates with its peer on an other device after the message has passed through the various layers.
Layer 1 : The lowest ;ayer is the physical layer, which is concerned with the transmission and reception of raw bits to and from the physical media use for communication.
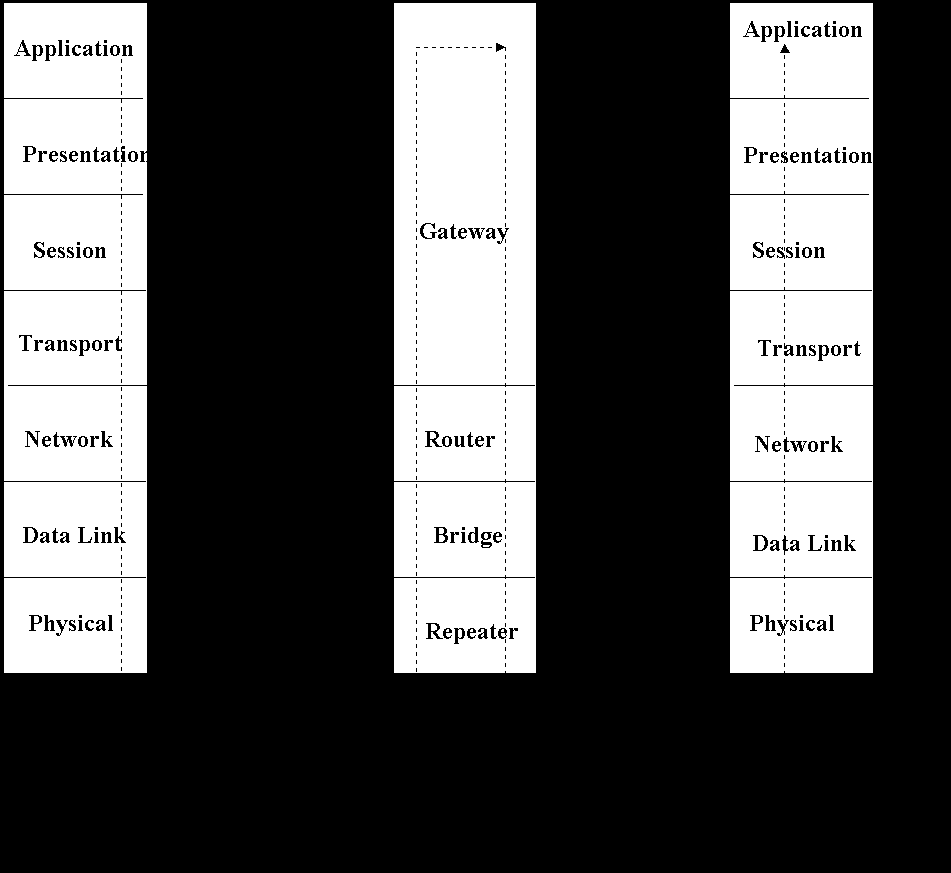
Layer 2: The data link layer provides for the errorless transmission and reception of frames of information. This layer defines a fixed communications path across a network based upon device addresses.
Layer 3: The network layer or interworking layer specifies the network topology based on user defined network addresses.
Layer 4: The transport layer provides end-to-end error protection and with the lower layer, forms a logically seamless data pipe for upper layers.
Layer 5: The session layer establishes computer communications for a specific task; for example, mail, file transfer and database query.
Larye 6: The presentation layer accomodates the way data are represented for example ASCII, or EBCDIC character sets.
Layer 7: The application layer completes the communications, for example, FTAM for file tranfer, access amd management.
Repeaters: Repeater regenerates signals to extend the distance they can travel and still remain recognizable to the receiving device. Repeater do this by amplifying the electrical signals. There is no isolation between LAN segments connected by a repeater, so a single extended LAN results. This means that repeaters can only be used to link LANs having the same physical level protocol. They do not control or route information, nor do they generally have management capabilities.
As the traffic load on LAN increases, an extended LAN may slow down under normal use. This occurs because a larger number of users must contend for the same amount of bandwidth. The slow response can be quite frustrating to the user who merely wants to send a message or print a document.
Repeaters also provide entry points for network manager. Repeaters are also taking on the added functions of linking different types of network media, fiber to coaxial cable, for example.
Bridges: When enough users are adversly affected by poor LAN performance, the situation can be devastating to the organization that relies on the productivity of its members for survival. A more intelligent device is required to extend the LAN while keeping the segments isolated. The device used is bridge which provides network extension, reading the individual LAN frames that are addressed to other segments.
A bridge connects LANs at a relatively low level, the MAC sublayer of data link layer. It routes by upper sublayer of data link. Most often, it connects LANs of same type but so,e bridges are available to interconnect Ethernet and token ring LANs. It keeps local traffic on LAN while allowing inter LAN traffic to be routed between LANs. By forwarding only frames addressed to devices on other segments, bridges increase the throughput of the LAN. It learns the device addresses on the LAN. The MAC-layer addresses are permanently assigned to attached stations in a flat addressing scheme. The bridge routing table stores the full 48-bit address of every station. Sice bridges operate at the data link layer of the OSI model, they are transparent to the higher layer protocols. Thus bridges can send traffic involving incompatible protocols across networks.
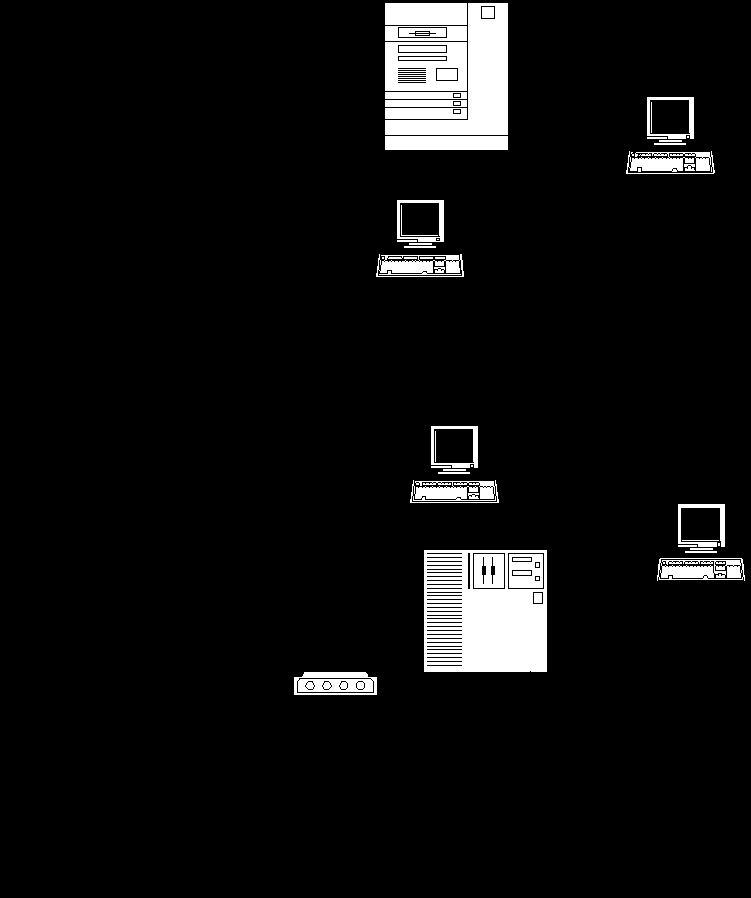
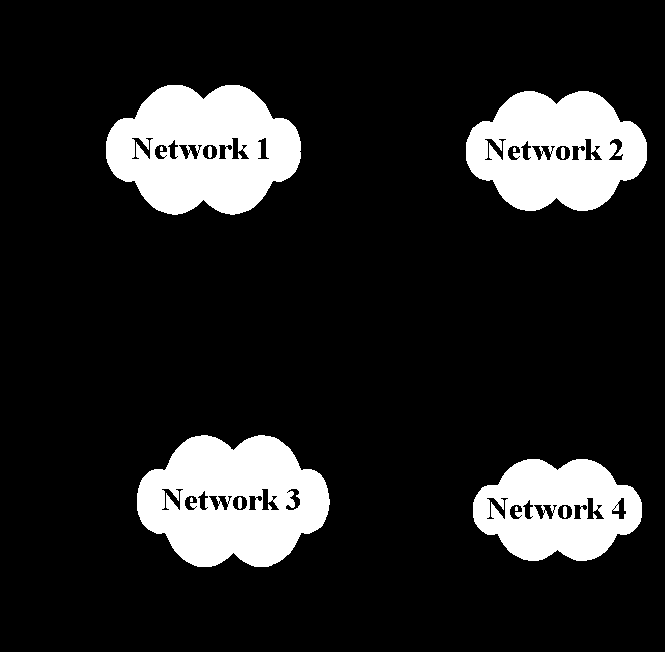
Routers: A router join networks at the network layer. It is protocol dependent device that distinguishes among different communications protocols and applies the appropriate routing technique to each. Routers may be used to build huge complex internetworks that rely on the network layer for efficient packet transmission. In fact, the router architecture is that of a packet switch, connecting multiple LANs and WAN packet facilities like X.25. The network layer protocol has its own source and destination information with which the router determines how to transmit packets to their destinations. The internet has systems of networks and routers called autonomous systems (AS) as shown in the figure.
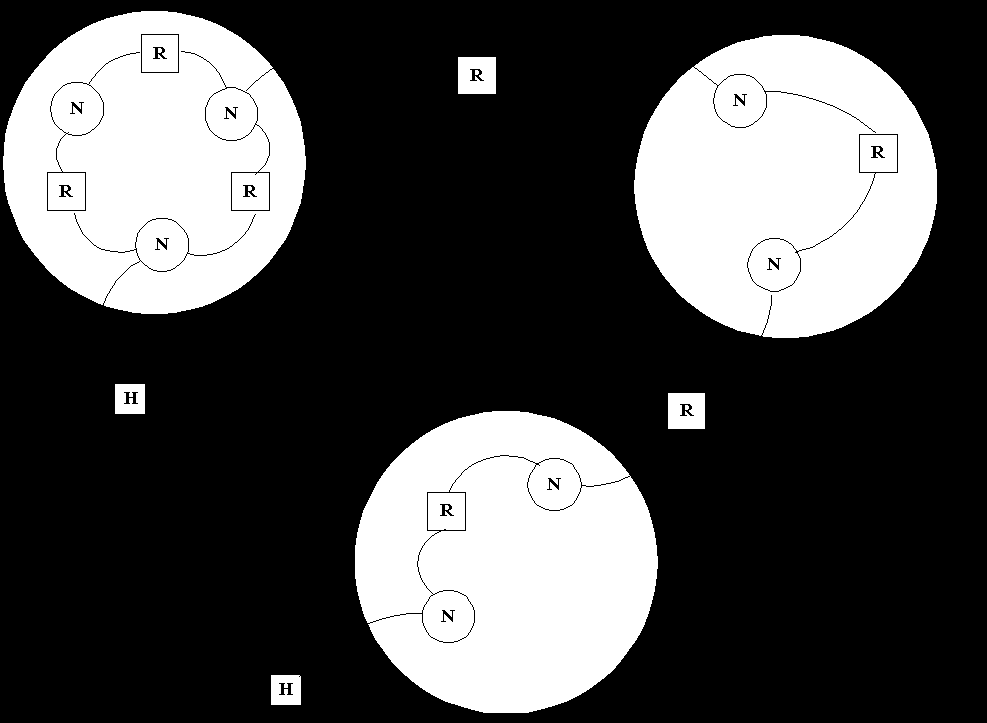
Within the AS, the routers communicate routes that relate to network connectivity. Within a particular network, the router keep track of host addresses. A router determines the network to which a forwarded packet is addressed, only routing on the host address if the source and destination on the same network.
When a packet arrives at the route, it is held in queue until the router finishes handling the previous packet. Then the router scans for the destination address and looks it up in its routing table. The roouting table lists the various nodes on the network as well as the paths between the nodes and their associated cost. If there is more than one path to a particular node, the router will select the most economical path.
If the packet is too large for the destination network to accept, the router segments it into several smaller packets, a process referred to as fragmentation in TCP/IP terminology. This capability is especially important in adjusting to WANs. With smaller packets, there is less chance that noise or other line impairments will corrupt the data. Even if that occurs, the error can be detected and a retransmission requested. For store-and-forward type packet networks, smaller packets actually result in higher throughput when frequent retransmissions occur. Consequently public packet switching networks have standarized on 128 byte packets rather than on 1,500 bytes frame used on ethernet LAN or the 576 byte byte packet standard used by Internet.
Despite the differences, the task of the router is similar to that of the bridge: to identify devices in the internetwork, setup the paths among LANs, and determine the criterial for data transport.
The network layer address more concise and hierarchical, however with part of address assigned to a group of stations designated as a network, subnetwork, or area and the remainder used to designate the particular station in the network or subnetwork. The result of hierarchical addressing is that router can store addressing information for networks with very large number of stations. For the same amount of memory, bridges are limited to networks with fewer stations. Router have detailed information about location of stations and use this to select among alternative paths to minimize transmission costs and avoid congestion. Network layer protocols contain a packet lifetime parameter or hop count field that prevents packet from loopin endlessly during transient network states.
There are two types of routing: static and dynamic. In static routing, the network manager configure the routing table. Once set, the paths on the network never change. This might not be sufficient for a LAN confined to small geographical area, but not for wide area networking. Although a static router will recognize that a link has gone down and issue an alarm, it will not automatically reroute traffic. A dynamic router on the other hand reconfigure the routing table automatically and recalculated the most efficient and/or economic path. Some routers even rebalance the traffic load.
Router operating in TCP/IP environments have userd dynamic routing algorithm called the Routing Information Protocol (RIP), which was originally developed for XNS. It was based on the TCP/IP Gateway/Gateway Protocol (GGP). RIP uses the number of hops a packet takes across router going from its source to destination as the primary criterion for determining path. The route with the least number of hops wins. Counting hops may not be the most efficient way to choose paths on a large network, however. Every router in the RIP system periodically updates its routing table by sending a copy to its neighbour whether changes need to be made or not, using time and bandwidth. A newer algorithm called the open shortest path first (OSPF) addresses these and other issues. OSPF issues update only when necessary, saving bandwidth. The update procedure of OSPF requires that each router on the network transmit a packet with a description of its local links to all other routers. Upon receiving this routing update packet, each router acknowledges it, and in the process, distributed routing tables are built from the collected descriptions. Since these descrition packets are relatively small, they produce a minimum of overhead. Upon a failure of link, updated information floods the network, allowing all the routers to si,ultaneously calculate new tables.
Gateways: As corporate divisions become more interrelated, the need to share files and communicate all kinds of information across diverse network makes it necessary to improve efficiency and productivity. Whatever the justification for linking dissimilar networks, an interconnection device is required to do the job. The gateway encompasses the functionality associated with all 7 layers of OSI reference model. Thus, gateways go beyond what other interconnect devices (e.g, bridges or router) do because they not only connect disparate networks but ensure that the transported data from one network are compatible with the data of others.
Physical gateway may consist of a two-port card, any number of which plug into the expansion slots of a microcomputer designated as the server. Gateways also offer parts that operate at different speeds. For instance, one port on the board may provide a synchronous 64kbps connection, while the other provides an asynchronous 19.2 kbps connection. More often, the gateway itself may not be a physical device but software that resides on a computer. PCs workstations or microcomputers serve as platform for gateway software that allows peer-to-peer communication among different computers removing the barrier of dissimilar communication architectures. The software could reside on each computer in a network, running in the background of other application programs. But the division of processing resources among the applications could degrade performance. For this reason, rather than split processing resources gateway often resides in a dedicated computer. The use of gateways represents a relatively new way for micro-to-mainframe communications by enabling the exchange of data between LAN based microcomputers and mainframes. The gateway does the necessary translation for communication with mainframe.
Consider a connection between an accounting department Ethernet LAN and an engineering department token-ring LAN. Despite their using different communications protocols, the two LANs are able to communicate by means of gateway. Suppose engineering uses Novell operating system and accounting uses Hewlett-Packard’s office Share. HP sells a Novell-compatible gateway that resides on a PC. Separate cards on PC plug into both LANs, allowing the gateway to serve as the physical connection between them.
TCP/IP: Higher -level network protocols determine how data are transferred from one place to another, specifying the communications procedure to be used and the format in which data are to be sent. TCP/IP is a suite of non-proprietary, high speed networking protocols. This suite includes transmission control protocol (TCP), the internet protocol (IP) and the user datagram protocol (UDP).
TCP/IP employs a multilevel, hierarchical networking structure, in which a backbone network links hosts and LANs so that local users can network easily and privately without affecting the larger networking environment.
The protocols that are concerned with the transport of information across the network, TCP/IP layers 3 and 4, have two primary functions. The Ips provide routing between networks and in some cases, within a particular network. The TCP forwards data delivered by the IP to the appropriate process in the receiving host. As a transport protocol TCP only guarantees end-to-end delivery. However, whether the host can understand the message depends on the compatibility of the higher layers.
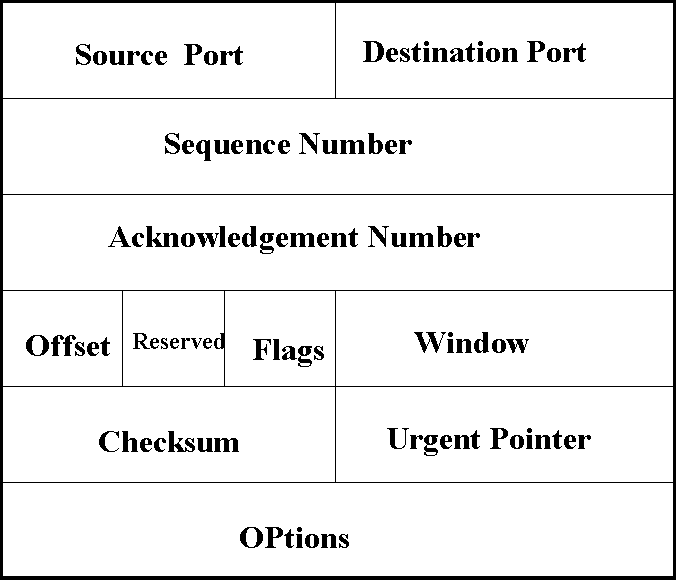
TCP defines the procedure for breaking up the datastream for upper layers into datagrams for transmission and ensuring the datagrams arrive at the proper location without errors. When it receives datagrams, the protocol defines how to reassemble them into proper order to reconstruct the original stream. If datagram arrive out of order, the protocol stores them and waits for the missing one to arrive. To accomplish this TCP breaks down the messages or datastream into a manageable size and adds a header to form a datagram.
The header consists of:
Source port (16 bits) Destination port (16 bits)
Calling and called TCP application. The port number is usually assigned by TCP. Whenever application makes a connection. However there are well known ports associated with standard services such as Telnet, FTP and SMTP.
Sequence number (32 bits )
Each datagram is assigned a unique sequence number that lets receiving device resemble the datagram in sequence to form the original data.
Acknowledgement number (32 bits):
indicates the identifier a sequence number of next expected byte. Its value is used to acknowledge all bytes tansmitted in the data stream up to that point.
Offset ( 4 bit):
Number of 32 bit words in TCP header. This is required because header may vary in length, according to option that are selected.
Reserved (6 bits):
Not currently used
Flag (6bits):
Indicates initialization or termination of a TCP session.
Window (16 bits):
Receive window size- indicate number of 8 bit bytes that the host is prepared to receive the TCP connection.
Checksum (16 bits):
To check error in received path.
Option:
Used by TCP software.
Internet Protocol (IP)
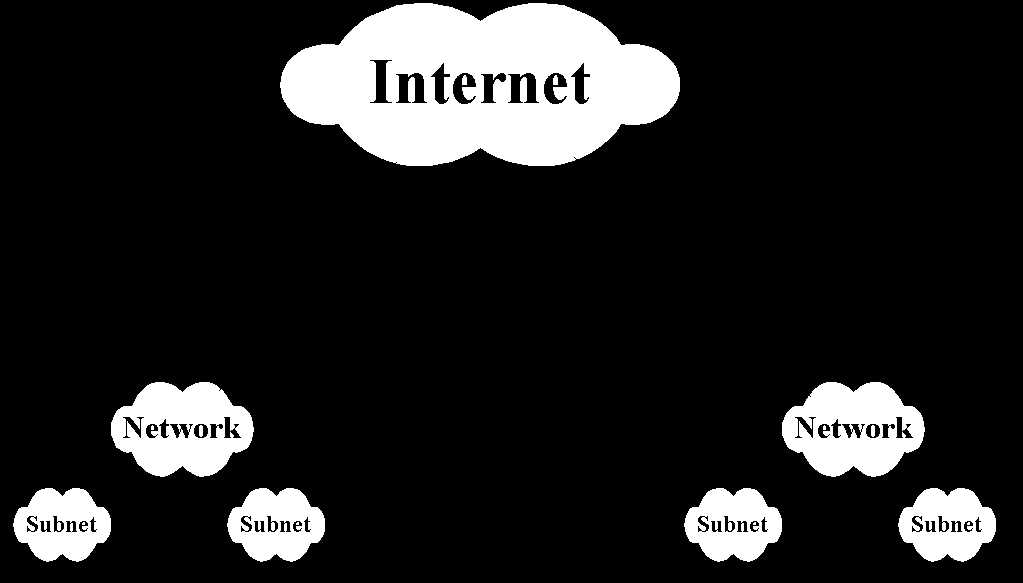
IP are especially important because they form the basis of the connectionless network service of OSI. IPs deliver data between different networks by connecting groups of autonomous systems consisting of subnetworks connected with gateways. Thus, the internet is composed of a series of autonomous systems, each of which is a centrally administered network or a series of subnetworks such as Ethernet Lan, X.25 packet or ISDN network, for example. Each autonomous system offers gateways that are used to connect to other autonomous systems. The gateways are the glue that holds all of these different networks together . The IPs define how subnetworks are connected and how the interconnection devices work.
IP defines how packets are routed from one subnet to another. Each node in the autonomous system has a unique IP address. IP adds its own header and checksum to make sure the datagram is properly routed. The process is aided by the presence of routing update messages that keep the routing tables current. Several different types of update messages are used, depending on the collection of subnets involved in a management domain. The routin tables list the various nodes on the subnets as well as the paths between the nodes and the path cost. If a particular node has more than one path, the most economical could be selected. If data packet is too large for the destination node to accept, it will be segmented into smaller packets, a process called fragmentation. This is especially important when transferring data from LANs to WANs. For e.g., a token ring LAN support 4,500 bytes, while X.25 packet networks generally support 128 bytes packet.
Domain Name Server (DNS):
The increasingly complex Lan networks go beyond the conventional relationship between the user and server; rather, there is a domain level between the user and a group of servers, migrating to complete transparency between users and group. The objective is to eliminate the need to tell the network where the messages should go and how to get them there. Many networks require that the user provide path information in the form of server names and patha descriptors before connection to resources can be made. This causes problems in large installations because the amount of information may be quite large, making the network unusable by all but the sophisticated users. The goal of the network directory system is to insulate the user or application from having to where things are physically located so that users and resources may be added, deleted or moved transparently. In effect, the network directory system insulates users or applications from the characteristics of underlaying communications system.
Common domain include commercial (COM), educational (EDU), governmental(GOV) and militaty(MIL). Each level of domain naming system has name assignment authority over the subdomains that it controls. Two character country codes are in the domain list. Examples include: YU(Yugoslavia), HU(Hungary), PO(Poland, JP(Japan), AU(Australia), FI(Finland), SE(Sweden), IT(Italy). Names on the internet are formatted according to the following hierarchy of domain and subdomains:
machine.suborganization.organization.domain
Request for translation of name into an internet address are sent to a domain name server. The server can either respond with the complete translation or with the name of another server to contact for that information.
Internet address:
The internet 32 bit addresses are administered by the network
information center (NIC) internet registry located at Stanford Research Institute (RSI).
If a locally administered private network is not connected to the larger internet, the
address can be arbitary. However, the use of arbitary addresses is not recommended, since
it can cause problems with later connection to the internet.
There are 3 classes of internet addresses, which can support networks of virtually any size. Class A addresses support upto 128 networks, each with upto 16,777,216 hosts, class B addresses support upto 16,384 networks, each with upto 65,536 hosts. Class C address support upto 2,000000 networks, each with upto 256 hosts. Class A addresses are assigned to the largest networks, such as MILNET, while class C addresses are typically assigned to the LANs of college campuses and small govermental contractors.
Internet protocols can be implemented over a wide variety of data link mechanisms. In each case, the data link layer makes all this using a bus topology and the CSMA/CD protocols, possibily with bridges to form an extended ethernet. X.25 networks may also constitute a subnetwork. X.25 provides a shared datastream by way of logical channels that provide non blocking access to host port. This arrangement saves the number of computer ports that must be provided, especially when using high data rates.
IP Transfer: When an IP node wishes to transmit information to another IP node, the IP module dispatches the data to the data link layer. The data link layer sends it across to another data link layer node on that network. To send the IP packet, the IP address must be translated into physical address for particular transmission medium. A packet of information is enclosed within an IP header. The IP datagram is then encapsulated with a subnetwork header, such as ethernet information.
IP Routing:
There are 3 cases of internet routing. Within a single network the IP module need only map the IP to the physical address and send the packet. X.25 subnetworks are able to shield the complexities of the underlaying data link from the IP module. Another IP routing scenario entails the routing of a packet to another subnetwork via the internet. This is done by consulting internet routing table which shows the destination net and the nearest gateway that can access the network. The host then routes the packet to the designated gateway, which in turn, consults its routing table for the location of the next gateway. Finally, the data are delivered to the destination network gateway, which delivers the packet to the designated host. An important IP concept is that routing decisions are made on the basis of networks, not the addresses of destination host.
A particular destination host is a part of a network, which is accessible by a gateway. A more sophisticated analysis of a host location within the target network is not available from the sending node. If the address of a non existent remote host is specified, an error message will not be generated until gateway connected to that network is reached. When that gateway discovers that the host address is not listed in its routing table, it will generate an error message.
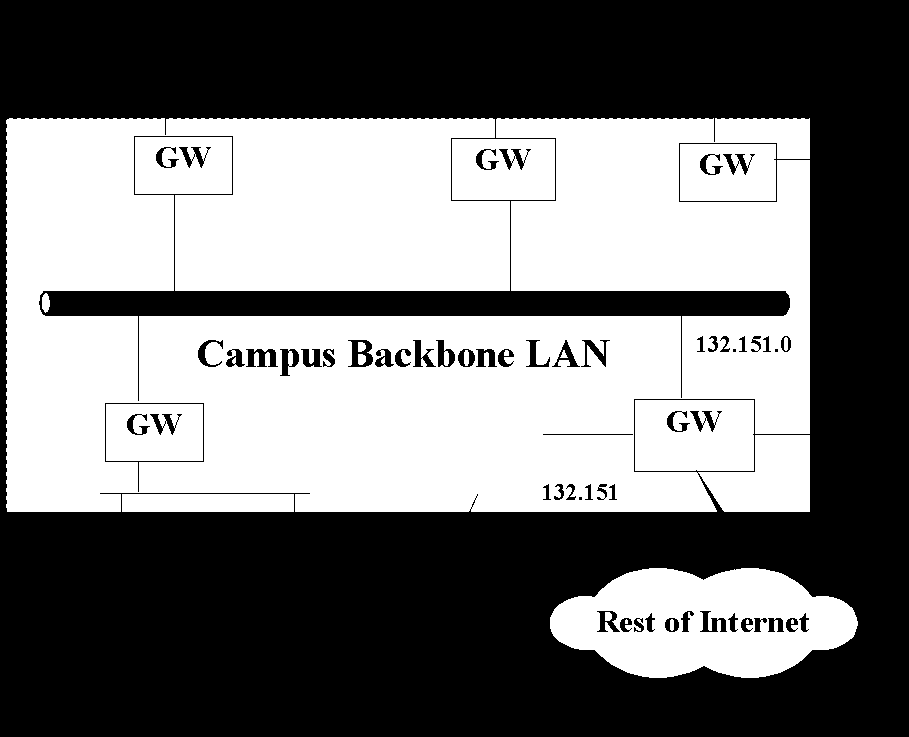
In addition to class A, B and C networks, IP also has encompassed the notion of the subnet within a class A or B net. A subnet is considered a part of an administrative domains such as a collection of campus nets that, to the outside world, looks like one net for routing purpose but in actually many networks.
Through TCP/IP, users may send/recieve messages to/from any nodes in real time. They can submit jobs or run programs on remote computers with which they have a valid user account. Files, documents, drawings, digitized speech and digital pictures can also be sent via the TCP/IP network. In order to utilize the Internet connection fully, the participating nodes in country may also adopt the use of leased communication lines to maintain 24 hours a day connection with the international gateway so that all applications with Internet are also made locally available.