Program Info
Intruder is a TSR program for debugging almost any program, driver and so on in real and
protected mode, monitoring interrupts, analyzing memory, system diagnostics, game cheating
and a lot of other stuff.
Intruder has been written to run under pure MS-DOS on a 386 or better processor (no Windows DOS-box).
If you're looking for a Windows debugger, take a look at WIntruder.
However, here is a feature list:
Simple Debugging:
Testing your programs, drivers or TSRs:
- free debugging (at any address, even ROM)
- terminate any running program
- restore old interrupt table
- free conventional or XMS memory
Cheating in games:
Additional features:
- user interface for your own plug-in modules (click here for UILM page)
- service function interrupt
- external debugger supported
Supported systems:
- real and v86 mode (VCPI)
- protected mode
- dos extender
Systems Requirements
Basically Intruder just needs some transistors and wires in a electrically healthy
environment to work. But if you don't design your own processors Intruder will accept the
following equipment:
- i386+ processor or compatible
- an IBM compatible computer
- MS-DOS 5.0 or above
- about 13 kB of conventional memory
- some XMS memory, depending on your configuration, but somewhere between 150 and 170 kB
- and of course an installed XMS manager
just a label
Download Intruder
You may download the unregistered version right here. If you want to register
contact us and look at the
Legal Stuff. However, there's no difference between the
registered and the unregistered version except a little motivation screen (for reminding you,
that there's a registered version available too). One other minor restriction
is that you cannot debug UILMs in protected mode.
Note: You won't be able to use all the nice features of Intruder (e.g. usage of the
TAB key during any input) without having read the manual.
You can contact us for sending your
suggestions and hints, if you have problems using Intruder, if you have found
a bug in the program (obviously this is the most improbable reason to write us) or
if you are a very nice person and want to register Intruder. For registering
download the file Register.txt above.
just a label
Legal Stuff
Intruder is Shareware. This means you can use the program for some time without paying for it.
If you like the program you should remember that programming is something that takes time. So wouldn't
it be fair if you'd register your copy of Intruder?! (Anyway, the little "motivation screen"
that pop's up every now and then is a "feature" the registered version is lacking.)
Some other restrictions: You can distribute and use (see the text above) the program as long as you:
- do not change the distribution file(s) or any part of it/them
- do not use it for commercial purposes or 'earning money' in general
- do not reengineer or disassemble any part of the program
Anyway we'd appreciate it if you'd send us an email
to tell us your opinion about the program and what should be improved.
just a label
Program Details
The Main Menu
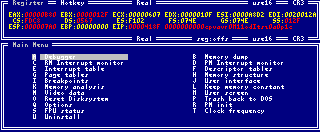 From the main menu you can reach all modules of Intruder by selecting the item or by
pressing the keyboard shortcut. On top of the screen you can find the register window (all 32bit)
with the current program and working status.
From the main menu you can reach all modules of Intruder by selecting the item or by
pressing the keyboard shortcut. On top of the screen you can find the register window (all 32bit)
with the current program and working status.
The Integrated Debugger
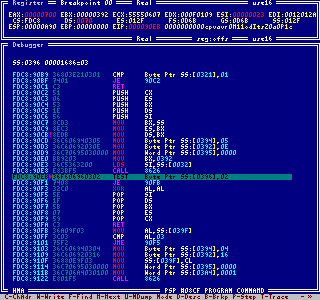 The integrated debugger is the actual core of the program. The colored disassembler allows
to find special opcodes much faster than with all the common colorless variants. Here you
have access to I/O ports, you can trace through the code, set breakpoints, modify the code
and register contents, load any programs for debugging and all the other things Intruder
can do.
The integrated debugger is the actual core of the program. The colored disassembler allows
to find special opcodes much faster than with all the common colorless variants. Here you
have access to I/O ports, you can trace through the code, set breakpoints, modify the code
and register contents, load any programs for debugging and all the other things Intruder
can do.
The Descriptor Tables
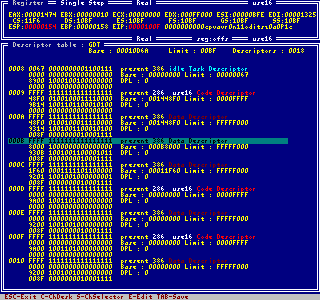 The descriptor tables offer a quick view to the protected mode memory arrangement. You can
choose between the global, local, interrupt or any other descriptor table in memory. A
single key punch stores the base address of a descriptor or the destination address of a
gate into a table for further work. And at last it is possible to modify or add descriptors.
The descriptor tables offer a quick view to the protected mode memory arrangement. You can
choose between the global, local, interrupt or any other descriptor table in memory. A
single key punch stores the base address of a descriptor or the destination address of a
gate into a table for further work. And at last it is possible to modify or add descriptors.
The Memory Structure
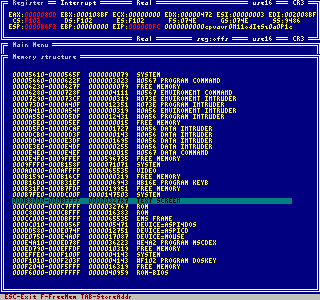 The memory structure gives an overview about all programs loaded. It displays position and
size of all allocated conventional memory and all XMS blocks. The memory position can be
stored in an internal table for further use. The entire array can be included in the
analysis array. And at last but not least you can free
any memory block, even xms.
The memory structure gives an overview about all programs loaded. It displays position and
size of all allocated conventional memory and all XMS blocks. The memory position can be
stored in an internal table for further use. The entire array can be included in the
analysis array. And at last but not least you can free
any memory block, even xms.
The FPU Status
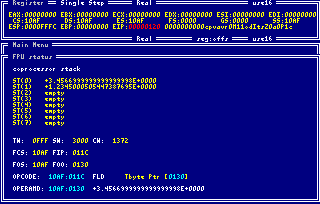 The fpu status displays the contents and status of the current floating point stack and the
last executed FPU instruction. In this way it is easy to observe the execution of your
coprocessor instructions.
The fpu status displays the contents and status of the current floating point stack and the
last executed FPU instruction. In this way it is easy to observe the execution of your
coprocessor instructions.
Interrupt Monitor
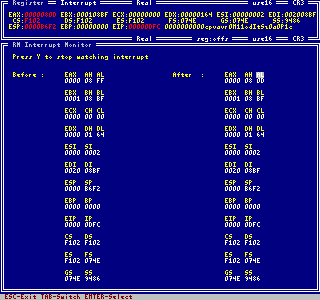 The interrupt monitor is one of the greatest features Intruder offers. It allows to hook a
special interrupt and to enter Intruder automatically when the monitored interrupt occurs.
Furthermore you can define some register conditions for entering Intruder. In this way
it is very easy to intercept special interrupt functions and/or special results returned by the
monitored function.
The interrupt monitor is one of the greatest features Intruder offers. It allows to hook a
special interrupt and to enter Intruder automatically when the monitored interrupt occurs.
Furthermore you can define some register conditions for entering Intruder. In this way
it is very easy to intercept special interrupt functions and/or special results returned by the
monitored function.
Video Data
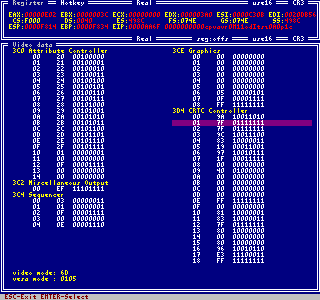 Here you can see and modify the contents of the video controller registers. This may is
helpful when working with special video modes. However Intruder needs to store these data
anyway.
Here you can see and modify the contents of the video controller registers. This may is
helpful when working with special video modes. However Intruder needs to store these data
anyway.
Memory Analysis
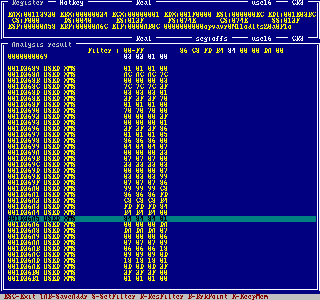 The memory analysis is a very powerful tool for analysing foreign programs such as games
(cheating) and so on. First Intruder generates a swap file of a specified memory array.
Then it is able to find these addresses which have been changed in a special way (e.g. all
data that have been decreased). The reduced data set is used for the next analysis. In this
way the number of possible data hits shrinks quickly. Afterwards you can set a breakpoint
at one of the memory locations found or even freeze the contents to a constant value.
The memory analysis is a very powerful tool for analysing foreign programs such as games
(cheating) and so on. First Intruder generates a swap file of a specified memory array.
Then it is able to find these addresses which have been changed in a special way (e.g. all
data that have been decreased). The reduced data set is used for the next analysis. In this
way the number of possible data hits shrinks quickly. Afterwards you can set a breakpoint
at one of the memory locations found or even freeze the contents to a constant value.
The User Interface
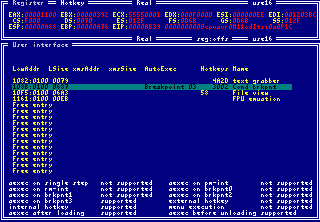 The user interface allows to load external modules and link them to Intruder. In this way
you can equip the program with functions it usually does not support. The modules can be
executed automatically e.g. when a special breakpoint or interrupt occurs to check out
some condition before entering Intruder. Furthermore they can be provided with hot keys (one
for internal and one for external usage). They also can be executed instead of disassembling
the code in the integrated debugger. So you can write and link your own
replacement or expansion for the disassembler.
Besides it is very easy to create modules because they are actually COM-style files
containing a special header (click here for UILM page).
The user interface allows to load external modules and link them to Intruder. In this way
you can equip the program with functions it usually does not support. The modules can be
executed automatically e.g. when a special breakpoint or interrupt occurs to check out
some condition before entering Intruder. Furthermore they can be provided with hot keys (one
for internal and one for external usage). They also can be executed instead of disassembling
the code in the integrated debugger. So you can write and link your own
replacement or expansion for the disassembler.
Besides it is very easy to create modules because they are actually COM-style files
containing a special header (click here for UILM page).
|